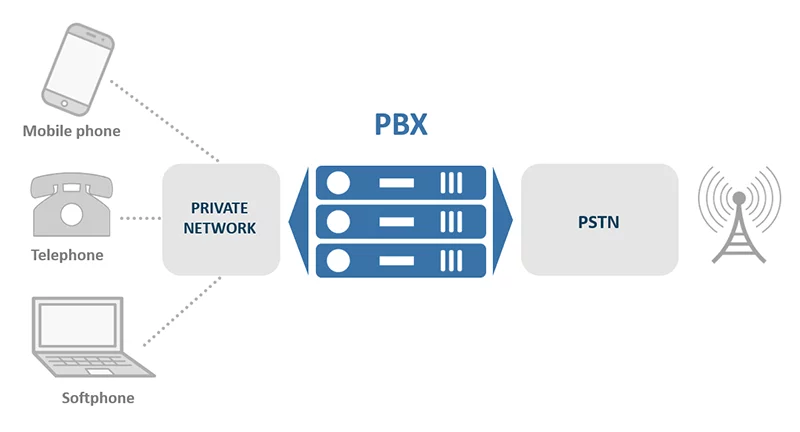
SD-WAN, or software-defined wide area network technology, is the next evolution of enterprise-wide area networks. Similar to software-defined networking (SDN), SD-WAN uses software to manage and control network resources and services. It is focused specifically on wide area networks, however.
A WAN connects two or more local area networks (LANs) in different geographical locations. WANs, for example, connect a LAN in the main office in New York to a LAN in a distant office in San Francisco. Software-defined wide area networks (SD-WANs) connect remote locations using virtualization technology rather than conventional hardware, such as routers.
This basic description, however, does not tell the whole story. The following explanation provides more details.
Through software and cloud-based technology, SD-WAN simplifies the distribution of WAN services to branch offices. Through software-based virtualization, network services are simplified.
SD-WAN enables IT and business managers to efficiently, securely, and conveniently deliver Internet-based networking. Moreover, it provides a cost-effective alternative for organizations of all sizes that suffer from lagging Internet connections.
SD-WAN: Understanding its importance
As organizations implement and understand cost savings and operational efficiencies, they have begun to adopt virtualization more quickly. There are several reasons why businesses are adopting SD-WAN. It is necessary to discuss the challenges facing businesses and their IT teams. We need to discuss the issues plaguing IT teams and how SD-WAN solves these networking challenges to understand why enterprises are embracing SD-WAN.
Issues related to hybrid networking
Enterprises can choose from a variety of routes, including multiprotocol label switching (MPLS), long-term evolution (LTE), and the Internet. A WAN should use all routes and choose the best path dynamically for users and applications to achieve the best service level agreement (SLA).
MPLS used to be the only transport method for businesses, but now, even if another transport system is introduced, it’s frequently used as a backup. It is because the combination of traditional WAN technology and routing protocols can be extremely challenging.
SD-WAN, however, can easily implement multiple transport mechanisms. Typical SD-WAN solutions are transport-agnostic and can utilize MPLS, 3G, 4G, 5G, LTE, wireless Internet, or some other form of transport. All of these routes are active-active, which means that when one node fails or slows down, another one in the network replaces it. Based on the policies set by administrators, the system will automatically choose the best route.
The cost of bandwidth is inflated
To be successful, companies must ensure the availability of their essential software and applications, whether they are customer-facing or employee productivity systems.
To be close to their clients and partners, companies continually deploy distributed architectures and business frameworks. Additionally, they expect that their application will be as reliable and efficient at the most distant branch location, connected by a WAN, as it is at the company’s headquarters or data center.
Enterprises have traditionally acquired and controlled private networks to achieve LAN-like efficiency. There are often multiple dedicated private networks for different applications.
On the other hand, these private networks are expensive. Due to these expenses, enterprises cannot support more challenging, real-time applications, such as voice over internet protocol (VoIP), video conferencing, and virtual desktops.
Businesses can use all of the available bandwidth on a site to use the inactive backup paths as active forwarding paths with SD-WAN. For example, email is not typically a time-sensitive application, and its bandwidth usage fluctuates. Therefore, an email application would not require a low-latency, high-quality route to deliver the service. This traffic will instead be detected and transferred over the least expensive path available in SD-WAN. In contrast, VoIP and video conferencing systems require low latency and a high-quality direction to meet the application’s SLAs. In SD-WAN, traffic is delivered over a route that meets the application requirements.
Taking security issues seriously
An organization’s security perimeter is no longer limited to the demilitarized zone of the data center as more applications are accessed through the cloud and Software-as-a-Service providers.
There is an overall growth and change of the WAN surface area. In recent security breaches, vulnerabilities have been found in the WAN. Traditionally, networking and virtual private networks (VPNs) are static, making them unstable, difficult to maintain, and slow to deploy.
SD-WAN, however, does not work that way. Since policies are transmitted from a central controller to the entire WAN Edge via an API, Encryption and app firewalling are security services that can be applied easily across the entire WAN Edge.
Migration to cloud computing
Taking advantage of cloud data centers and SaaS applications, businesses need the best architecture. In addition to daily application issues and branch deployment issues, IT must prepare for a seismic change in the computing world.
The standard in the past was client-server applications. Today’s applications are a lot more powerful and feature-rich. Traditionally, businesses have used private networks to provide reliable, high-performance, and highly accessible connectivity to software hosted within an organization’s headquarters and private data centers.
Connecting each branch to a cloud-based application is ideal with an Internet-based cloud-based system. No company can afford to give up the reliability, efficiency, and flexibility of a private network. An Internet-based cloud-based system is a near-ideal method of connecting each branch to the various cloud applications. Because no company can afford to give up the reliability, efficiency, and flexibility of a private network.
By profession, Neomi Rao is a Digital Marketer and blogger by passion. She is enthusiastic about exploring the modern-day tech landscape thanks to her tech background and experience in Digital Marketing. In addition, she is passionate about writing on software-defined networking& SD-WAN technologies.













Leave a Reply